This blog post contains my solution to the challenges of OverTheWire: Bandit. This wargame is aimed for beginners. You just need to complete upto level 12 now (because you are just a beginner now 🙂 )and we can continue it later.
NOTE: In have replaced the actual passwords with “*” so that you can solve the challenges by yourselves.
THINGS NEEDED: Linux and a little brain.
Level 0
This was a simple challenge in which I had to login in via ssh to the target machine using the credentials “bandit0:bandit0” with the help of your terminal.
To log in fire up your terminal and use the command
ssh bandit0@bandit.labs.overthewire.org -p 2220
It will then ask for the password which is bandit0.
Then read the password from the file readme on the home directory. The password in the file is for the bandit1 user which is the user for the next level.
bandit0@melinda:~$ ls
readme
bandit0@melinda:~$ cat readme
*************************
Level 1
Login via ssh and use the password you got in level 0.
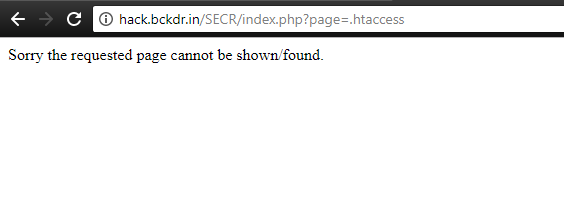
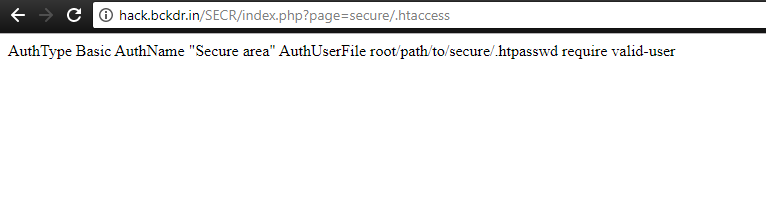
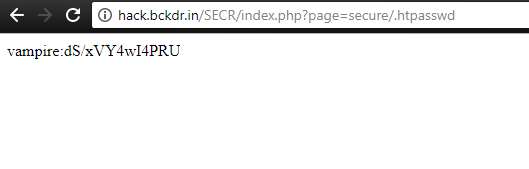
The goal for this level was the following “The password for the next level is stored in a file called – located in the home directory”. So in this level, there is a file called “-” in the home directory and it contains the password for the next level.
bandit1@melinda:~$ ls
-
bandit1@melinda:~$ cat ./-
*************************
Again a very simple challenge, all I did was use “./” to the absolute path of the file.
Level 2
The goal for this level is the following “The password for the next level is stored in a file called spaces in this filename located in the home directory”, another challenge getting players of bandit use to working with Linux.
bandit2@melinda:~$ ls
spaces in this filename
bandit2@melinda:~$ cat spaces\ in\ this\ filename
************************
You can also use tab to complete the file name for you.
Level 3
The level goal for this level is “The password for the next level is stored in a hidden file in the inhere directory.”, again a very simple challenge for anyone with any Linux experience. For this challenge I’m going to add the “a” switch to my “ls” command which will display all files including hidden files and the by using “.” as part of the filename in Linux specifies that the file is a hidden file.
bandit3@melinda:~$ ls -la
total 24
drwxr-xr-x 3 root root 4096 Nov 14 2014 .
drwxr-xr-x 172 root root 4096 Jul 10 2016 ..
-rw-r--r-- 1 root root 220 Apr 9 2014 .bash_logout
-rw-r--r-- 1 root root 3637 Apr 9 2014 .bashrc
-rw-r--r-- 1 root root 675 Apr 9 2014 .profile
drwxr-xr-x 2 root root 4096 Nov 14 2014 inhere
bandit3@melinda:~$ cd inhere
bandit3@melinda:~/inhere$ ls -la
total 12
drwxr-xr-x 2 root root 4096 Nov 14 2014 .
drwxr-xr-x 3 root root 4096 Nov 14 2014 ..
-rw-r----- 1 bandit4 bandit3 33 Nov 14 2014 .hidden
bandit3@melinda:~/inhere$ cat .hidden
********************************
Level 4
We are told the password is somewhere in the inhere directory and is the only human readable file in the directory. Let’s see what file types we have.
bandit4@melinda:~$ ls
inhere
bandit4@melinda:~$ cd inhere/
bandit4@melinda:~/inhere$ ls
-file00 -file01 -file02 -file03 -file04 -file05 -file06 -file07 -file08 -file09
bandit4@melinda:~/inhere$ file ./-*
./-file00: data
./-file01: data
./-file02: data
./-file03: data
./-file04: data
./-file05: data
./-file06: data
./-file07: ASCII text
./-file08: data
./-file09: data
bandit4@melinda:~/inhere$ cat ./-file07
********************************